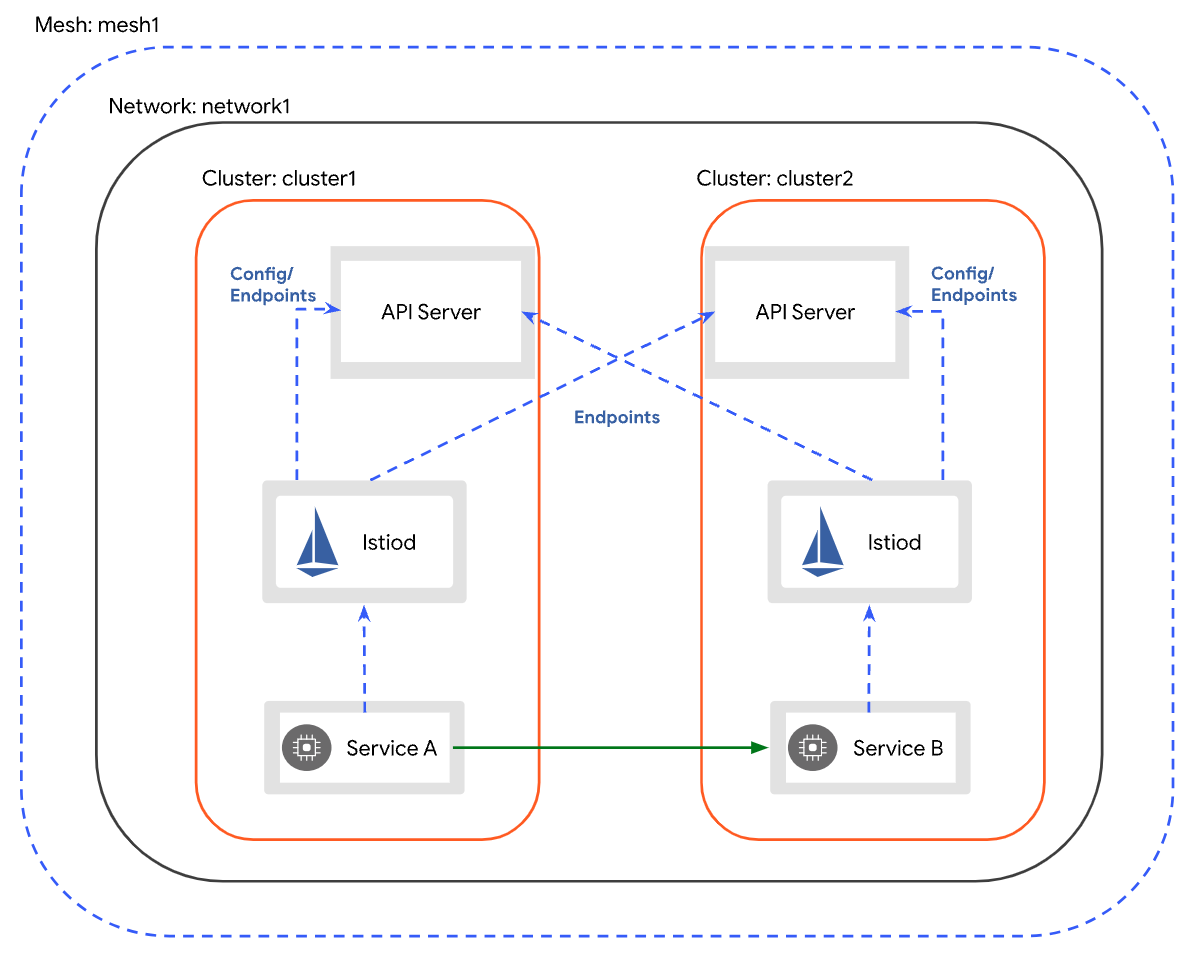
基于安全容灾考虑,生产K8S集群是多可用区。多可用区集群必然涉及跨可用区调用,由于是海外业务,使用的是AWS云,AWS内部跨可用区流量不像国内云厂商跨可用区流量不收费,是需要收费而且特贵。
基于成本和容灾考虑使用Istio的地域负载均衡功能,优先调度到同可用区,出现问题时调度到另一可用区。
现使用 kind 在本地创建一套多节点集群,通过标签模拟多可用区场景。
由于办公电脑是M1,而Istio1.13并不支持M1,所以选用Istio1.16,K8S1.24版本
创建多节点集群模拟跨AZ
kind配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
| mkdir -p multicluster
cd multicluster
cat << EOF > kind-cluster1.yaml
kind: Cluster
apiVersion: "kind.x-k8s.io/v1alpha4"
networking:
apiServerAddress: "172.26.128.224" # 本机IP,可不设置。
podSubnet: "10.10.0.0/16"
serviceSubnet: "10.11.0.0/16"
nodes:
- role: control-plane
image: registry.cn-hangzhou.aliyuncs.com/seam/node:v1.24.15
- role: worker
image: registry.cn-hangzhou.aliyuncs.com/seam/node:v1.24.15
kubeadmConfigPatches:
- |
kind: JoinConfiguration
nodeRegistration:
kubeletExtraArgs:
node-labels: "topology.kubernetes.io/region=az01,topology.kubernetes.io/zone=az01"
- role: worker
image: registry.cn-hangzhou.aliyuncs.com/seam/node:v1.24.15
kubeadmConfigPatches:
- |
kind: JoinConfiguration
nodeRegistration:
kubeletExtraArgs:
node-labels: "topology.kubernetes.io/region=az02,topology.kubernetes.io/zone=az02"
EOF
|